Information Security Management Program Template

Refer to appendix a.
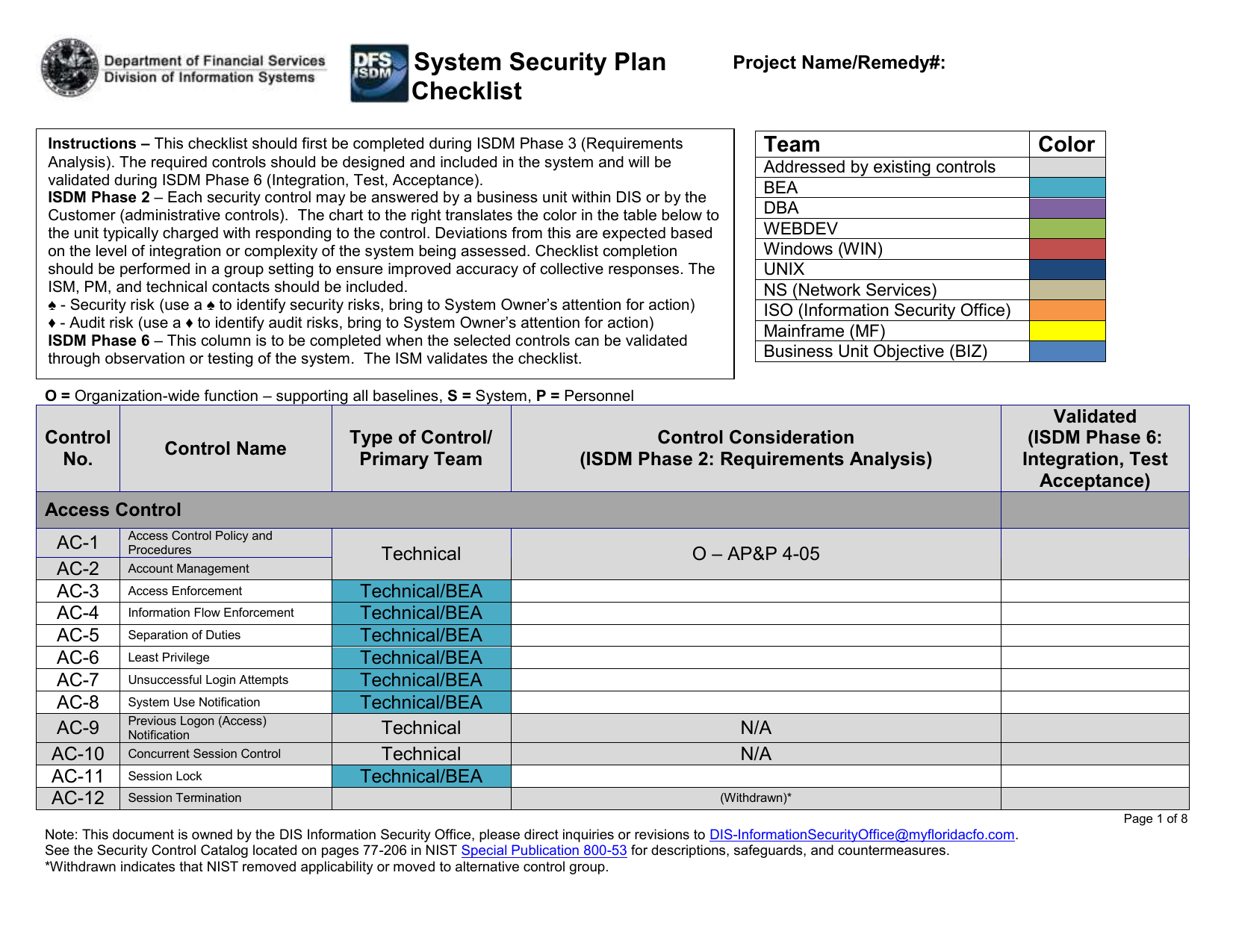
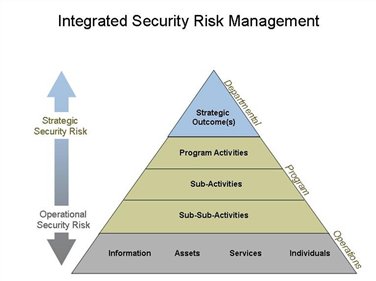
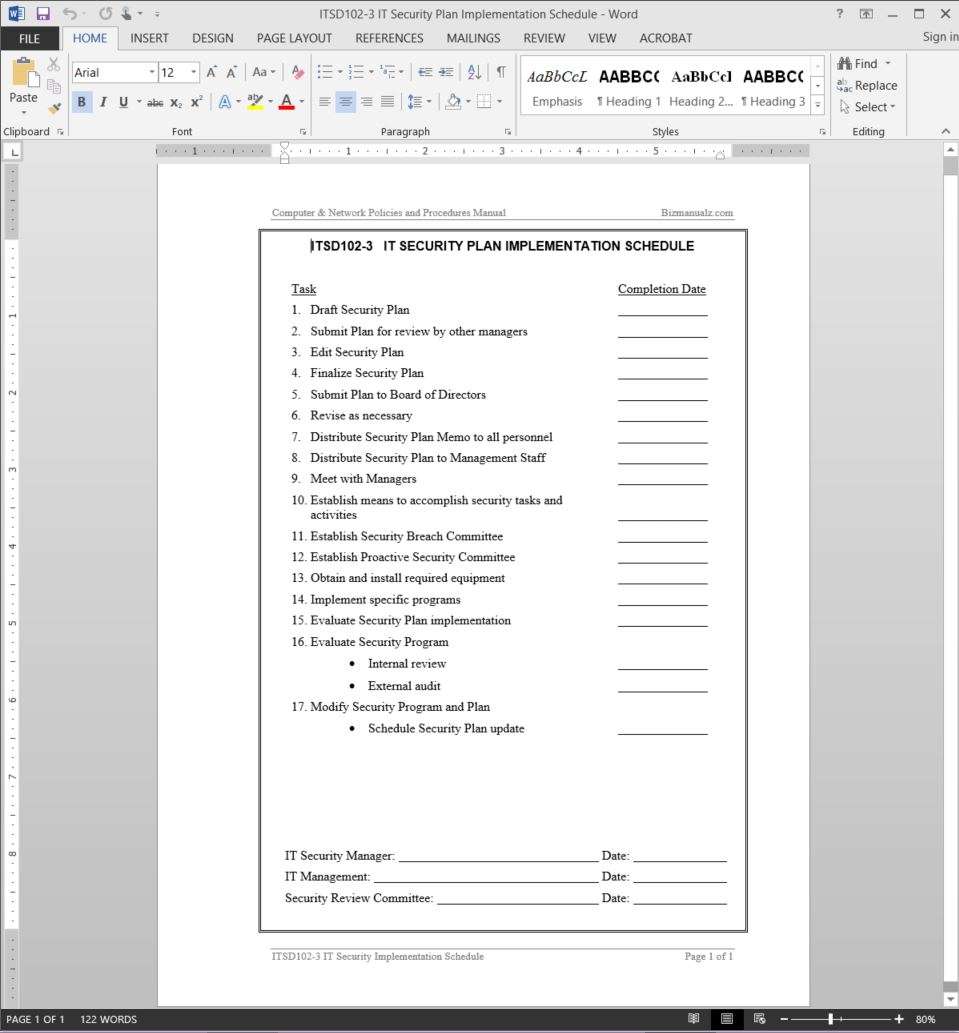
Information security management program template. Enterprise information security program plan. Role responsibility specific functions information asset owners often the 1program unit and management affiliated with a particular program responsible for the following within their areas of program responsibility. Youll find a great set of resources posted here already including policy templates for twenty seven important security requirements. This it security management plan template enables departments to describe how the confidentiality integrity and availability of information will be ensured through the implementation of it security measures.
Setting up an information security program is a daunting task. The sample security policies templates and tools provided here were contributed by the security community. Available resources for a template to complete the information classification activity. Comprehensive written information security program wisp is to create effective administrative technical and physical safeguards for the protection of personal information of residents of the commonwealth of massachusetts including our employees and to comply with our obligations under 201 cmr 1700 the regulations.
An effective information security cybersecurity program requires a strategic approach and an information security cybersecurity policy is the foundation for success. A solid policy is built with straightforward rules standards and agreements that conform to industry best practices and regulatory requirements. Templatesit has already done that for you so that you can focus your time on setting up the information security program right. Information classification documents can be included within or as an attachment to the information security plan.
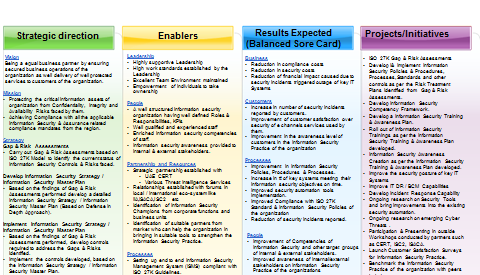
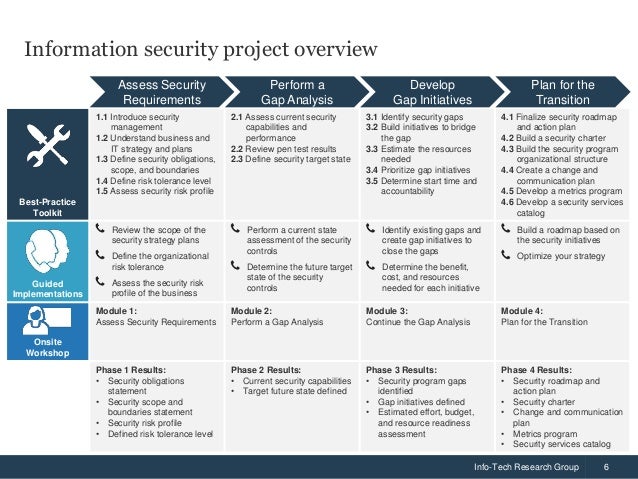
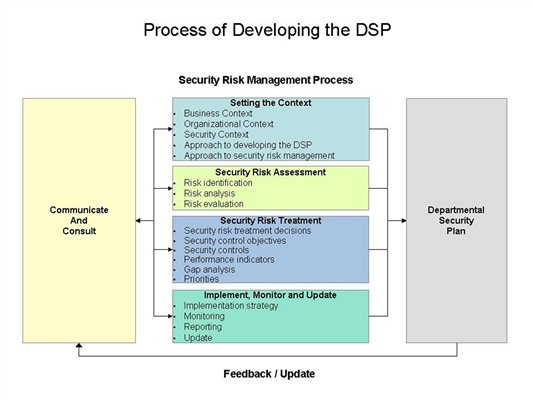
Practice shows that a multi phased approach to creating an isrm program is the most effective as it will result in a more comprehensive program and simplify the entire information security risk management process by breaking it into several stages. Information security program management standard simm 5305 a 9 january 2018. Overview control areas related policies. The ultimate goal of the project is to offer everything you need for rapid development and implementation of information security policies.
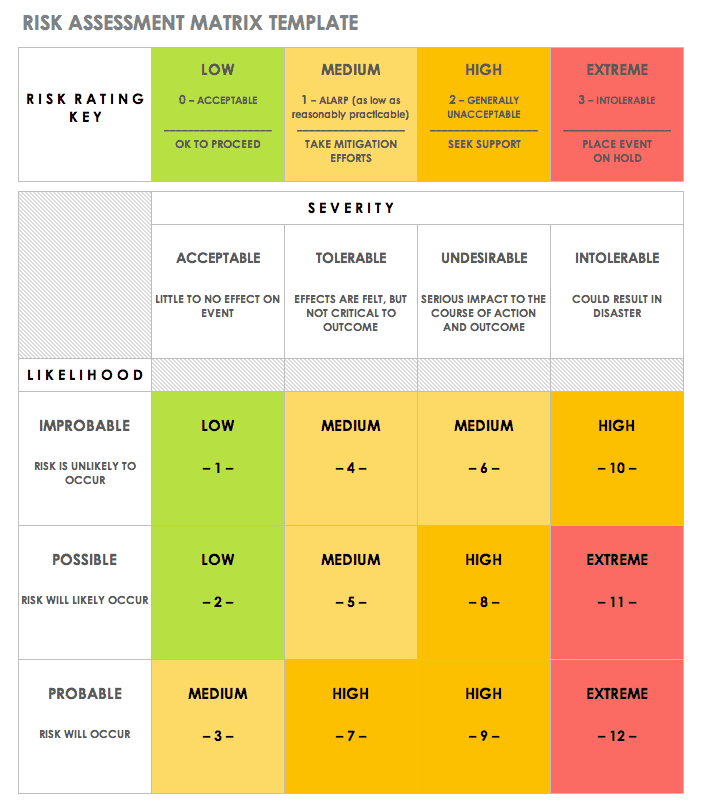
What are the steps for creating an effective information security risk management program. Additionally a sample is provided. Overview and security program objectives. Feel free to use or adapt them for your own organization but not for re publication or.