Iot Certificate Management

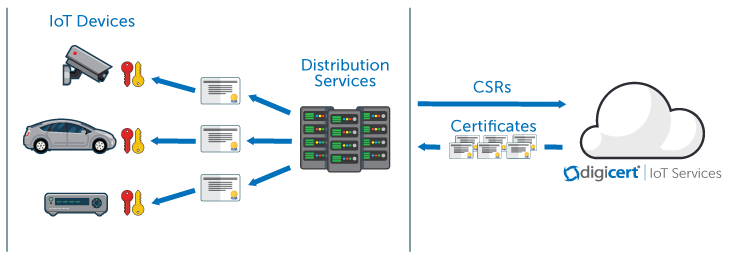
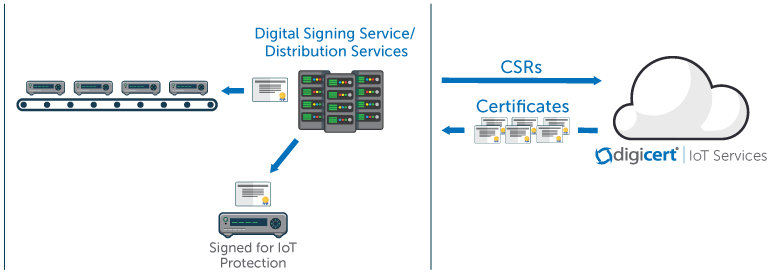
In house pki management is not a viable option for iot devices owing to their sheer number.
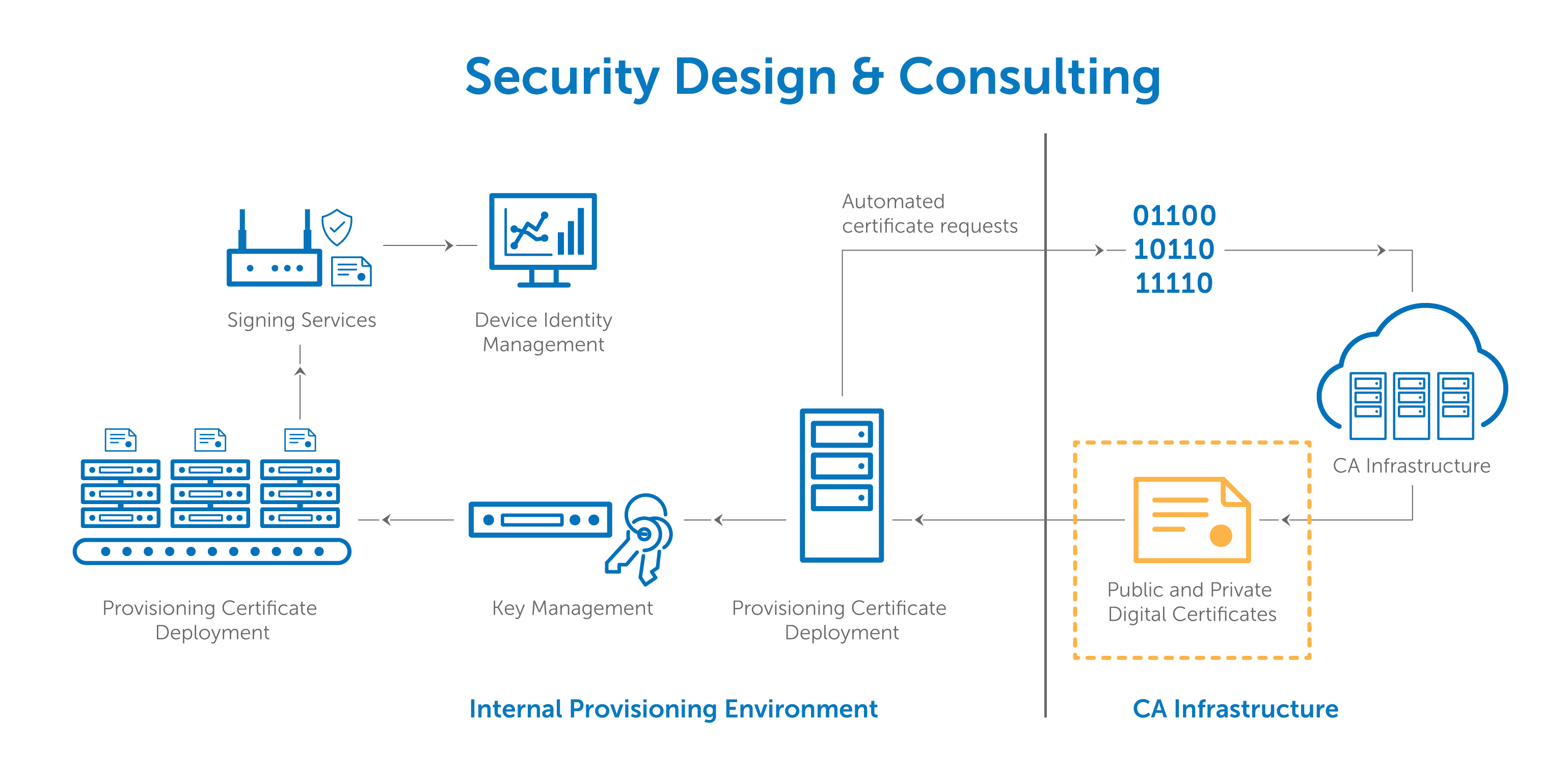
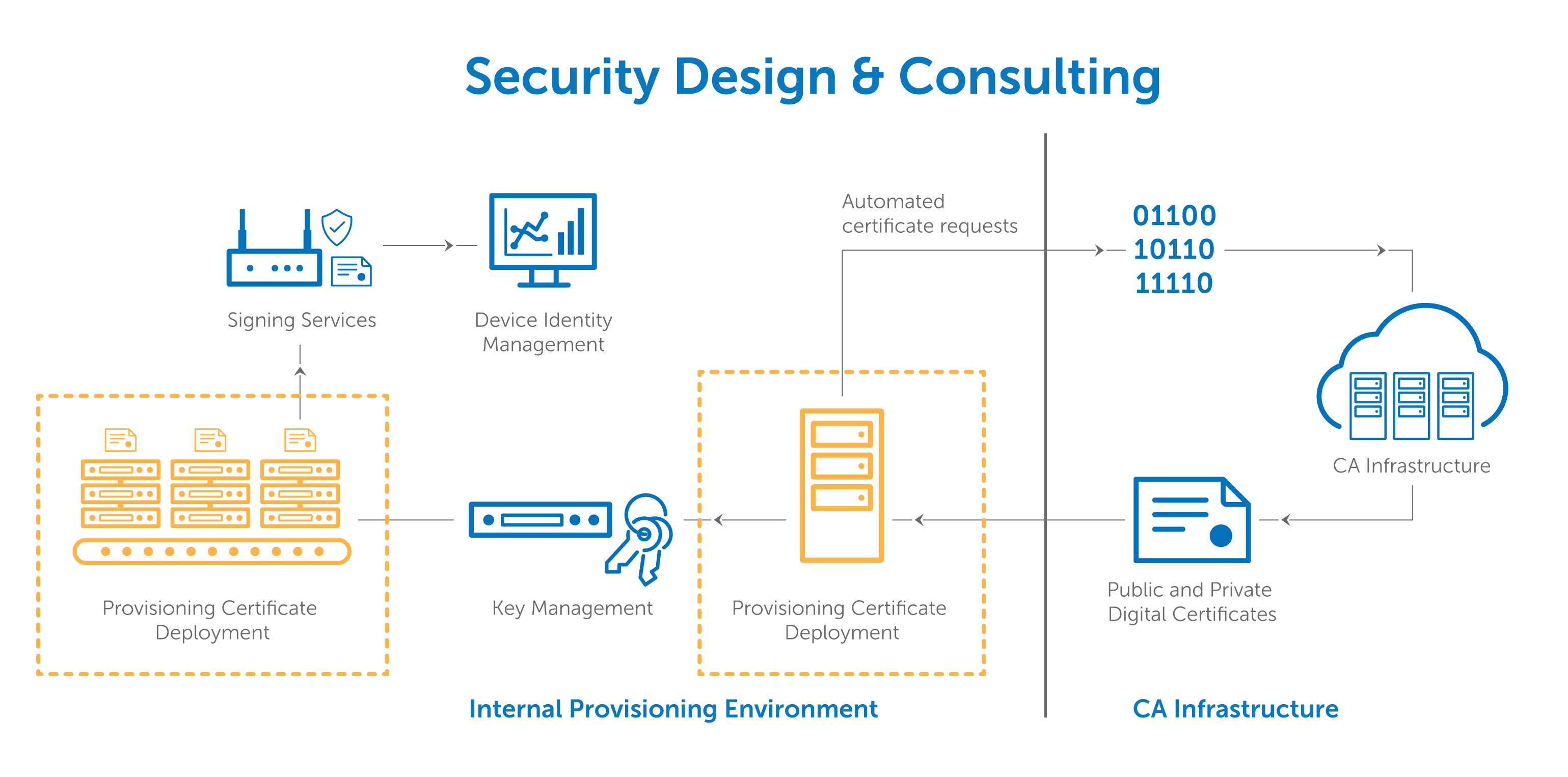
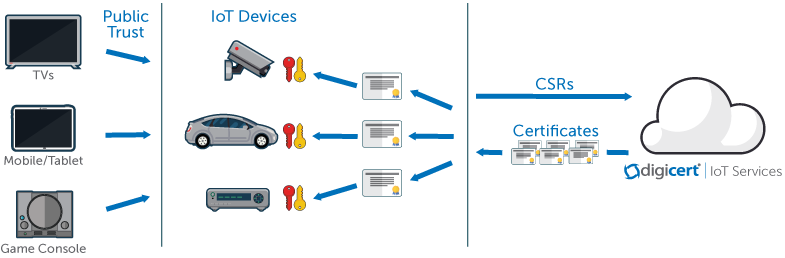
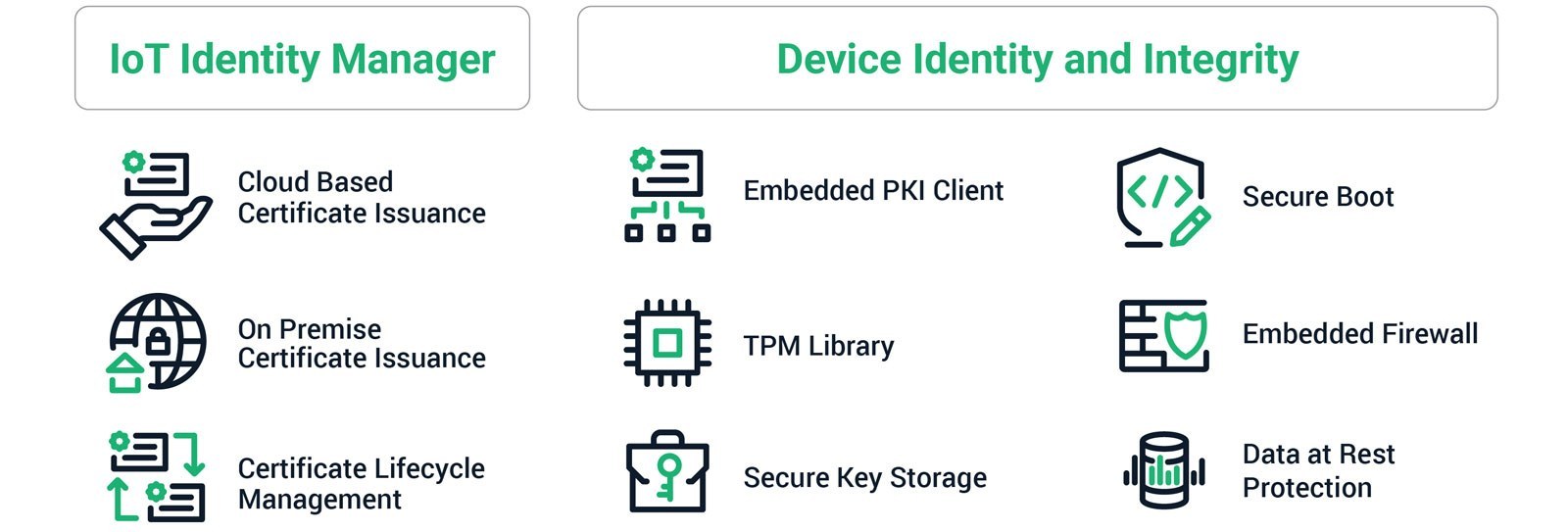
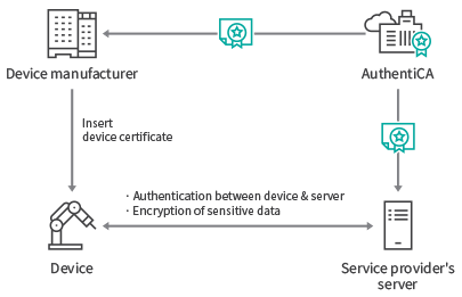
Iot certificate management. Key management is about the policies and practices for creating developing transferring and accounting for cryptographic items ie keys and certificates for iot devices and systems. Ssl certificates can have a great impact on memory if you do not consider the type of certificate being used in iot solutions. Each pki certificate is a unique identifier and greatly aids in creating trusting relationships between customers and businesses. Pki certificates are issued from a ca certificate authority which creates and manages them.
The program comes with a copy of my iot decision workbook and iot product strategy briefing. A factory could easily be using thousands of iot devices and managing their certificates in house levies an unnecessary strain on resources. Moreover even one expired or compromised certificate left undetected can wreak havoc on the whole network. The iot product manager certificate program also includes.
Key management strategy guidelines. Here are a few things to consider when creating a key management strategy. Templates and hands on exercises. Your devices can use x509 certificates to authenticate with aws iot core.