Pki Certificate Types

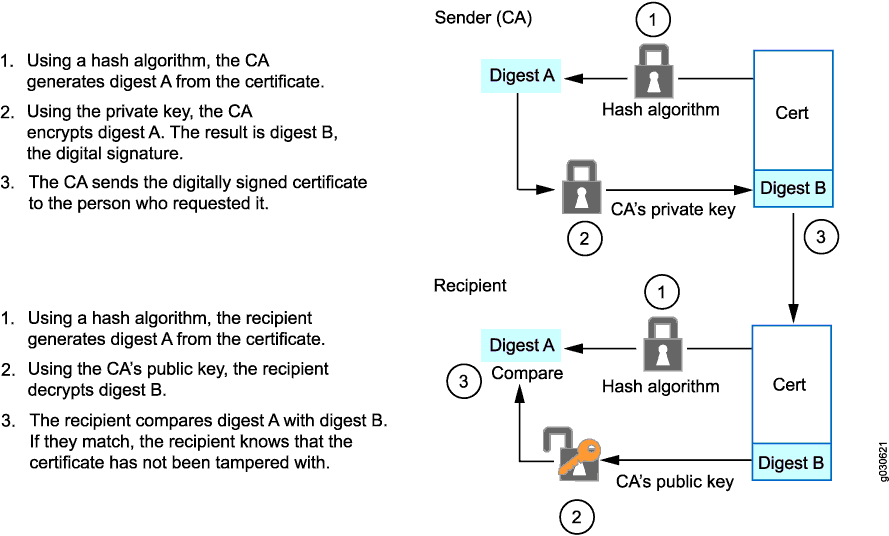
The certificate signing request is then submitted to a certificate authority to provide validation.
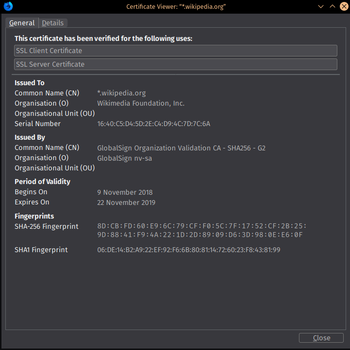
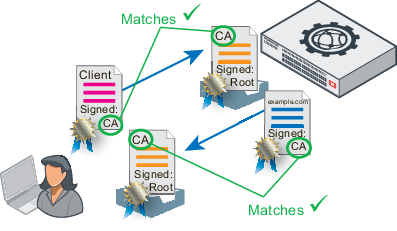
Pki certificate types. In a typical public key infrastructure pki scheme the certificate issuer is a certificate authority ca usually a company that charges customers to issue certificates for them. By managing keys and certificates through a pki. This certificate must be exported in a public key certificate standard pkcs12 format and the password must be known so you can specify it to the client when you specify the pki certificate. At its core an x509 certificate is a digital document that has been encoded andor digitally signed according to rfc 5280.
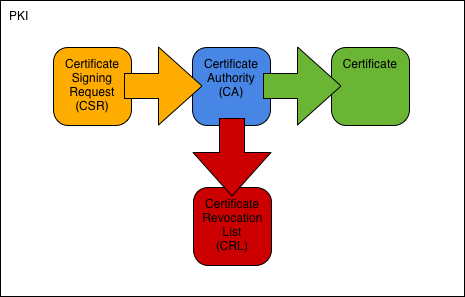
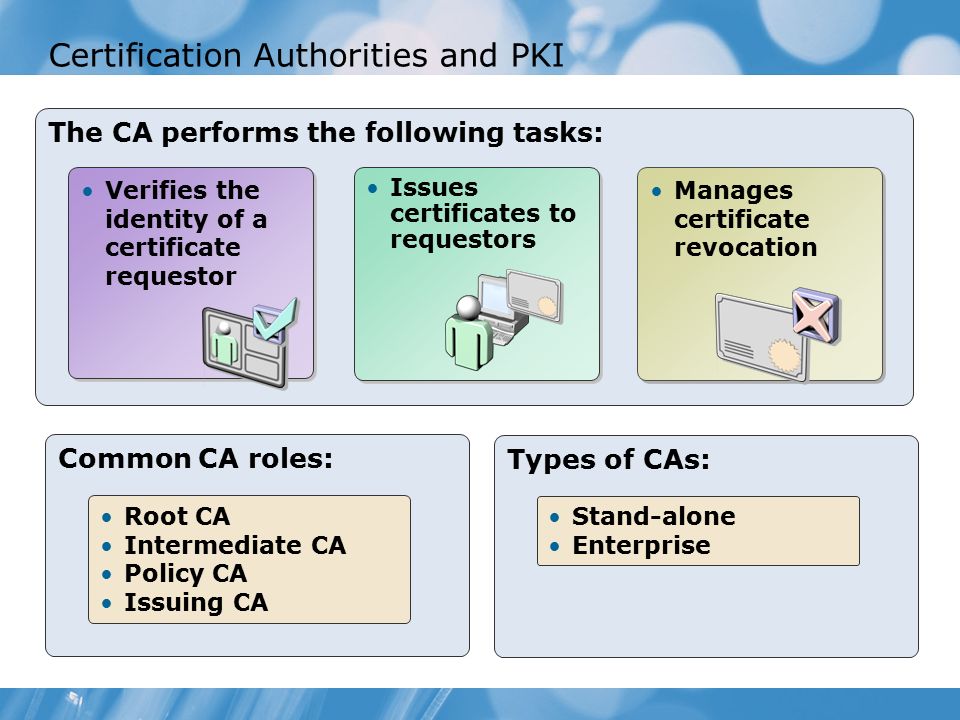
The pki creates digital certificates which map public keys to entities securely stores these certificates in a central repository and revokes them if needed. Top the comprehensive system required to provide public key encryption and digital signature services is known as a public key infrastructurethe purpose of a public key infrastructure is to manage keys and certificates. Pki certificates are all x509 certificates with different key usage configurations. Separate pkcs7 certificate bundles are also included for each root ca for relying parties who may wish to only accept certificates issued with the key and signature hash combinations eg.
Types of public key infrastructure certificates. A public key infrastructure pki is a system for the creation storage and distribution of digital certificates which are used to verify that a particular public key belongs to a certain entity. This zip file contains the dod pki certification authority ca certificates in pkcs7 certificate bundles containing either pem encoded or der encoded certificates. Singleone tier hierarchy one tier hierarchy consists of one single ca.
By contrast in a web of trust scheme individuals sign each others keys directly in a format that performs a similar function to a public key certificate. In a hierarchical pki a typical deployment there are generally three types of hierarchies one tier two tier and three tier. The keys are at the heart of a pki certificate and how it works either as an ssltls product or as an email and authentication certificate. In fact the term x509 certificate usually refers to the ietfs pkix certificate and crl profile of the x509 v3 certificate standard as specified in rfc 5280.
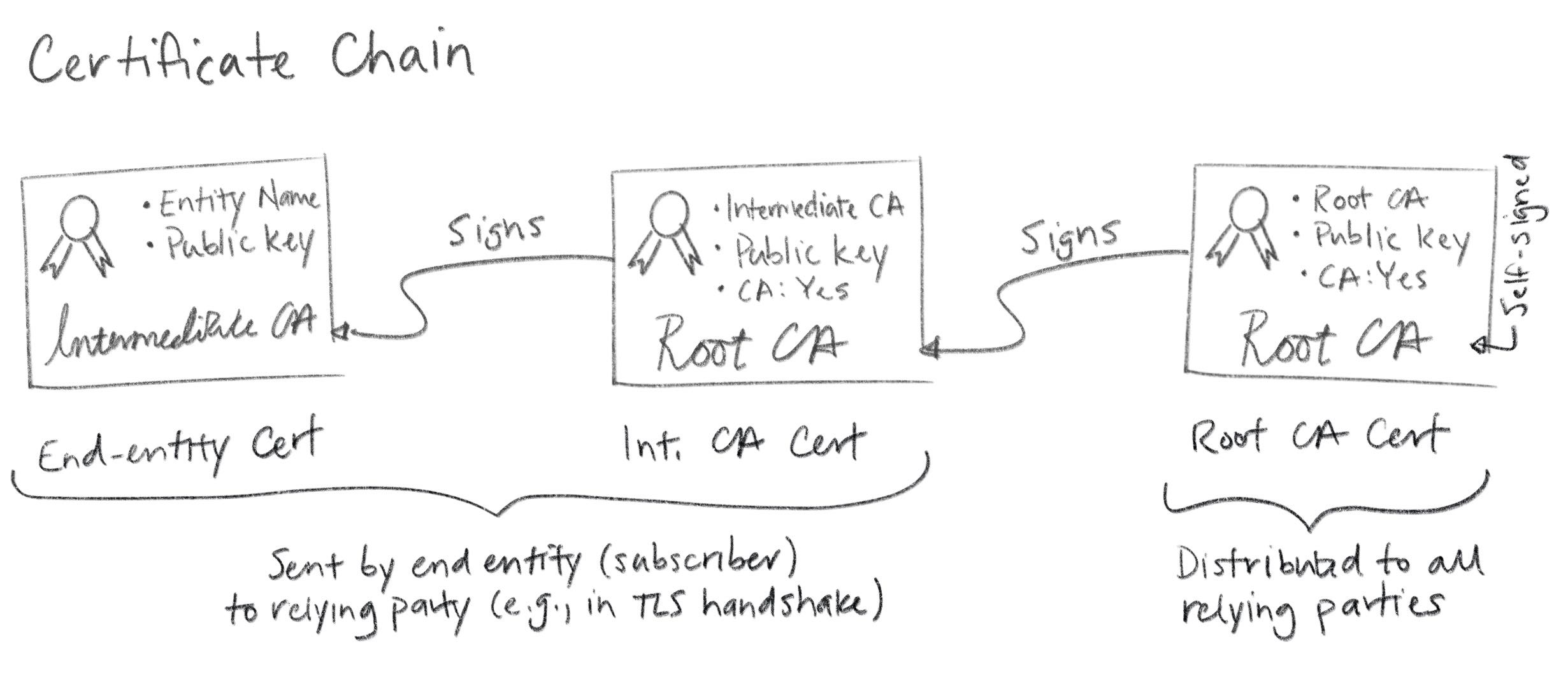
There are three types of ssl certificate available today. Rsa 2048sha 256 issued by a given root. It uses certificate chains and ca hierarchies to create a system where entities can be authenticated using digital certificates and signatures. This is the entire pki trust model.